arp
Address HWtype HWaddress Flags Mask Iface
iPhone-von-me.fritz.box ether 12:55:05:30:3c:df C wlp3s0
android-abcdefghijklmno ether 11:66:3f:71:04:d6 C wlp3s0
fritz.box ether 00:11:3f:46:37:c2 C wlp3s0
Blupiblu.fritz.box ether 71:88:cc:bb:dc:a6 C wlp3s0
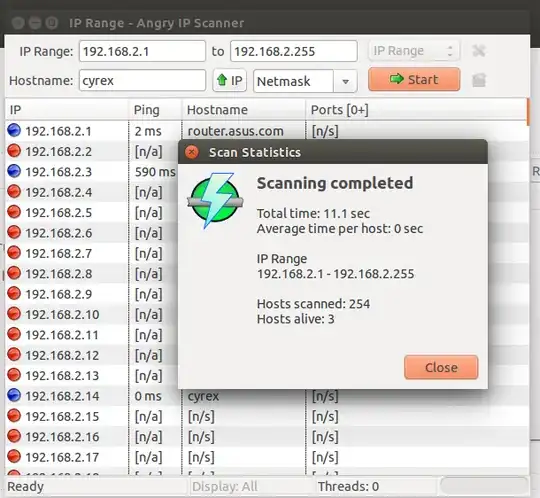
ip neigh
ip neigh and hosts. NO nmap / sudo required.
Building on this, you can build a Python script:
#!/usr/bin/env python
"""List all hosts with their IP adress of the current network."""
import os
out = os.popen('ip neigh').read().splitlines()
for i, line in enumerate(out, start=1):
ip = line.split(' ')[0]
h = os.popen('host {}'.format(ip)).read()
hostname = h.split(' ')[-1]
print("{:>3}: {} ({})".format(i, hostname.strip(), ip))
Download via
wget https://gist.githubusercontent.com/MartinThoma/699ae445b8a08b5afd16f7d6f5e5d0f8/raw/577fc32b57a7f9e66fdc9be60e7e498bbec7951a/neighbors.py